How to setup Active Directory Authentication in Rhythmyx
Content
How to Connect to LDAP Browser
- Connecting using AD Explorer
- Connecting using JXplorer
- Connecting using Active Directory Studio
- How to configure in Rhythmyx Server Administrator to Authenticate to Active Directory
- Configure Directory Services: Authentications
- Configure Directory Services: Directories
- Configure Directory Services: Directory Sets
- Add a New Security Provider
- Add an Active Directory user to a Role
- Test Authentication in Rhythmyx using Active Directory Credentials.
Connect to LDAP Browser
As a first step you have to verify whether you can able to establish connection with Active Directory server using provided credentials. Additionally, if you are not provided with Active Directory’s Users distinct Name / object name which is the node where user information can be accessed in Active Directory’s Directory Information Tree (DIT). You have to identify Users node/object from DIT. This object name is needed for configuring Provider URL selector – Base DN attribute in Rhythmyx Server Administration. You need a LDAP browser for this purpose. If you don’t have LDAP browser already installed you can obtain from any of following URL:
Open source LDAP browsers:
- Jxplorer
- AD Explorer
- Developers using Eclipse IDE can use – Active Directory Studio an eclipse plugin for LDAP and Active Directory. Installing this plugin will add LDAP perspective using which you can establish LDAP/AD connections and explore DIT.
http://directory.apache.org/ : http://directory.apache.org/studio/update/2.x
Connect to Active Directory using AD Explorer and Explore DIT:
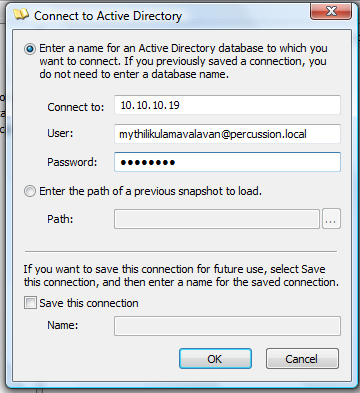
Step 1: Connect to Active Directory
- Enter following attributes value:
- Host name
- User Name / DN
- Password
- Click OK.
Note: You can save the connection by selecting checkbox “Save this connection”.
Connection attributes:
Connect to: Host Name
Example:
ADTest / IP Address (10.10.10.19 for percussion.local)(changed to 10.10.10.21)
User Name: Qualified Distinct Name (DN) or User domain format login
Example: DN : CN=Users,DC=percussion,DC=local
Domain format user name : username@percussion.local
Password: Password provided for Active Directory access.
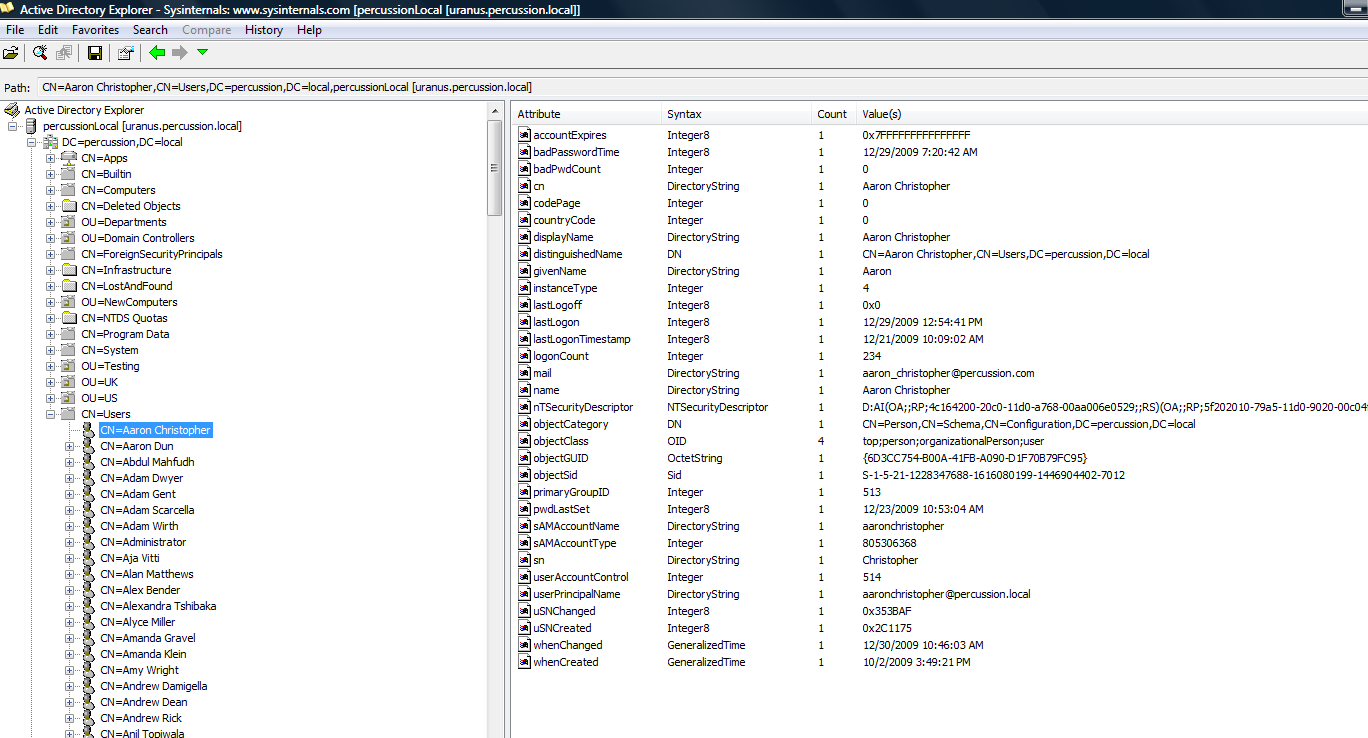
Step 2: If authentication is successful, you would see an Active Directory explorer populated with Directory Information Tree (DIT) where you can able to browse the information stored in Active Directory.
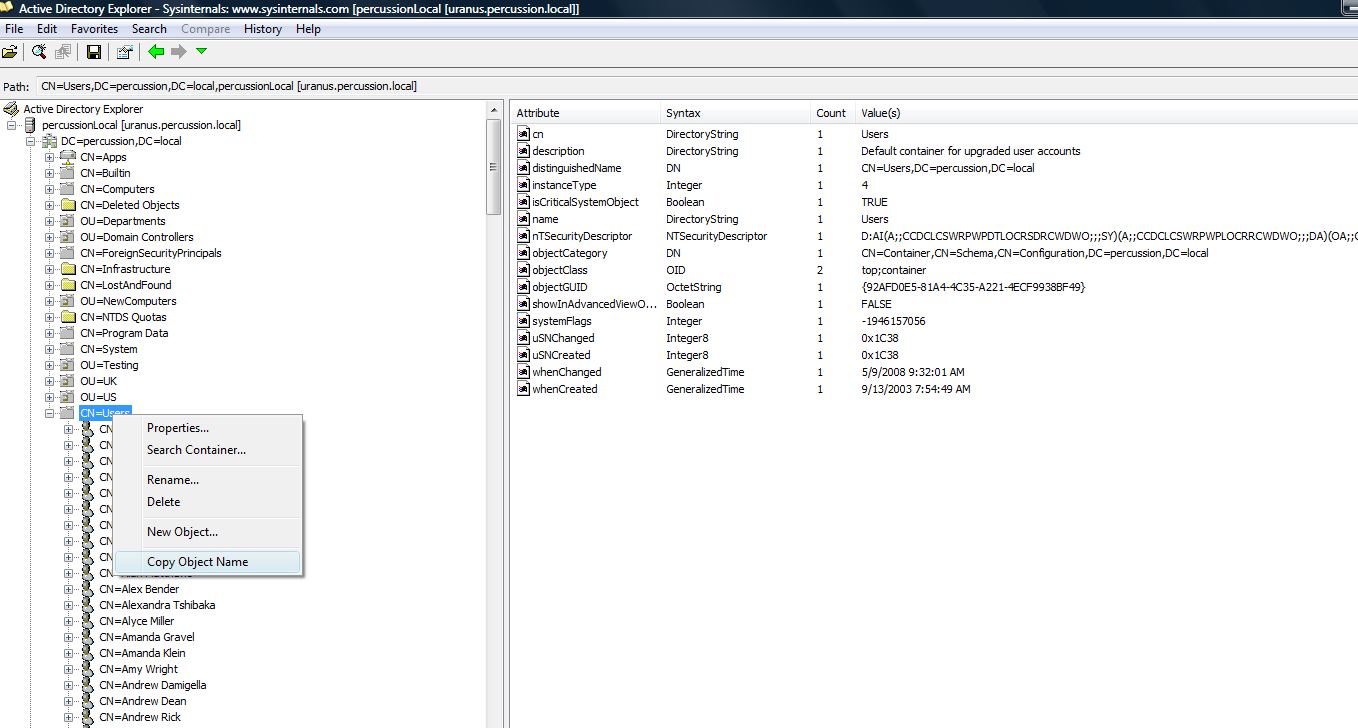
Step 3: Identify the object/node (cn=users) in Directory Information Tree where user information is stored which we will be using for authentication. Right click the node and select copy Object Name and have the value saved using in a text editor. You need this object name for configuring Provider URL selector – Base DN attribute in Rhythmyx Server Administrator.
Sample object name: For percussion.local - CN=Users,DC=percussion,DC=local
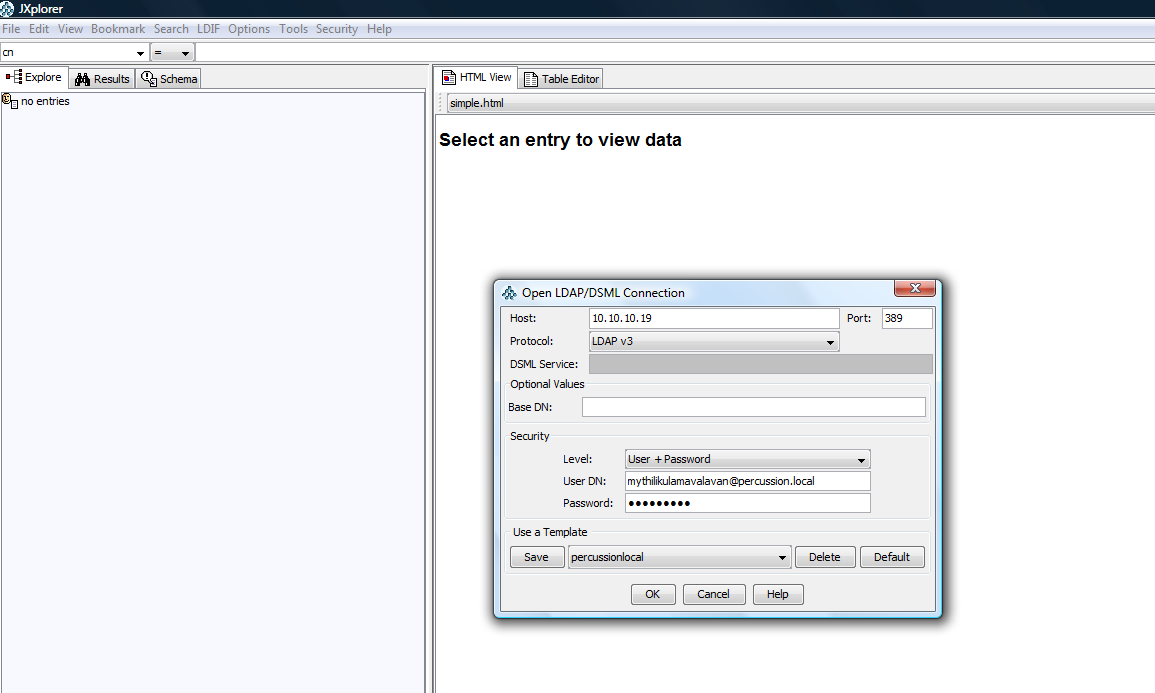
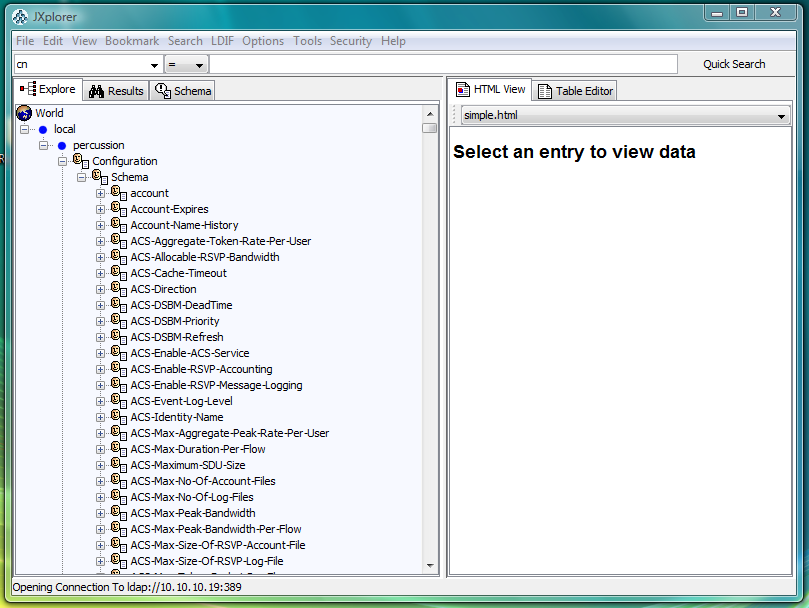
Connect to Active Directory using JXplorer - LDAP browser:
Following is the screen-shots for connecting to Active Directory using JXplorer.
Configure Rhythmyx Server Administrator to connect to Active Directory
For configuring Rhythmyx Server to authenticate from Active Directory following configurations need to be performed by logging as admin in Rhythmyx Server Administrator.
Step 1: Configure Directory Services: Authentications.
Step 2: Configure Directory Services: Directories.
Step 3: Configure Directory Services: Directory Sets.
Step 4: Add a New Security Provider.
Step 5: Add an Active Directory user to a Role.
Step 6: Test authentication by Logging in to Rhythmyx.
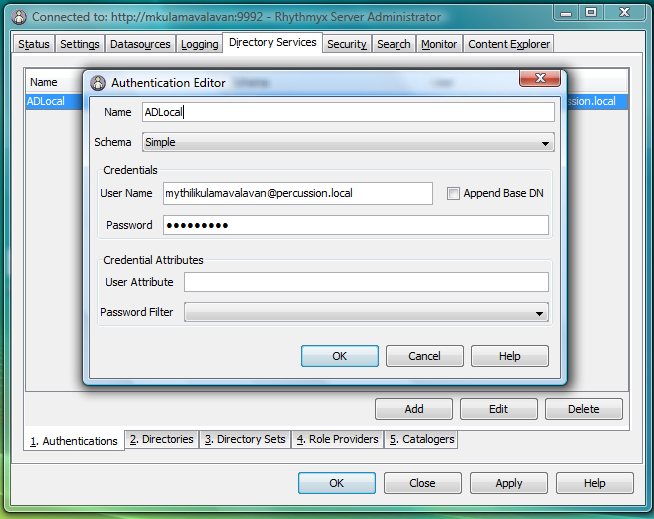
Step 1: Configure Directory Services: Authentications
- Select Directory Services tab /Authentications tab and click Add button.
- Enter following attribute values:
- Name (any valid name)
- Schema : Simple
- User Name : DN or valid user name
- Password - { Enter the same password that you used for the LDAP browser}
- Click OK.
Step 2: Configure Directory Services: Directories
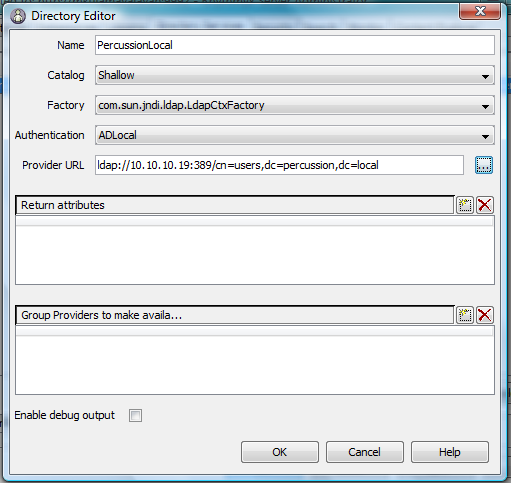
- Select Directory Services tab / Directories tab and click Add button.
- Enter following attribute values:
- Name: (any valid name)
- Catalog : Shallow
- Factory : com.sun.jndi.ldap.LdapCtxFactory
- Authentication: Name of Authentication created in previous Step 1.
- Click ellipse button to configure provider URL.
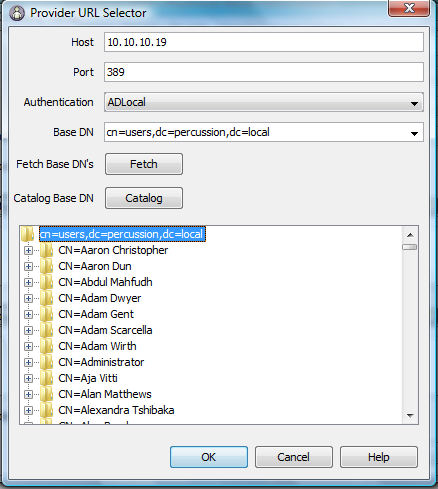
- Enter following attribute values in Provider URL Selector Dialog:
- Host : Host Name / IP Address (For Percussion Local IP is 10.10.10.19)
- Port : Active Directory Server port number (default – 389)
- Authentication: Authentication Created in Step 1.
- Base DN: Object/ Node of Users information value obtained from LDAP Browser or DN if one provided to you.
- Press the Fetch button to test the Authentication.
- Click Catalog button CN=Users node.
- Click OK.
- Directory Editor’s Provider URL will be updated as shown in Directory Editor image.
- Click OK
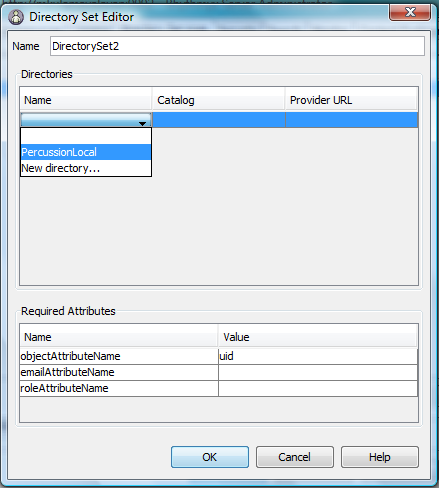
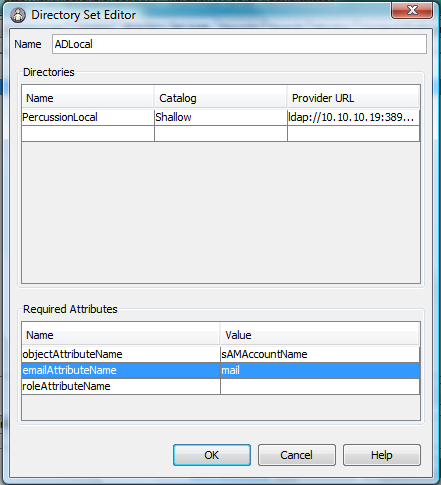
Step 3: Configure Directory Services: Directory Sets
- Select Directory Services tab / Directory Sets tab and click Add button.
- Enter following attribute values:
- Name: (any valid name)
- Directories: Double click new row under Name Column and choose Directory created in Step 2.
- Required Attributes :
- objectAttributeName: Attribute name of User Account Name in DIT. (For percussion.local it is sAMAccountName)
- emailAttributeName: Attribute name of User email in DIT. (For percussion.local it is mail)
- Click OK.
- Click OK.
Step 4: Add a New Security Provider
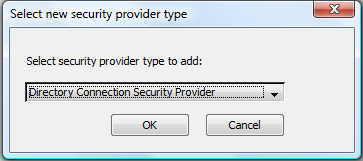
- Select Security tab/ 1. Security Provider tab and click New… button.
- From Select new security provider type to add drop down, select Directory Connection Security Provider option and click OK.
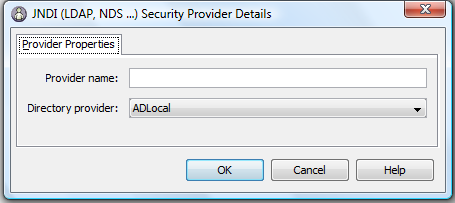
- In the Security Provider Details Dialog enter any valid Provider Name and click OK.
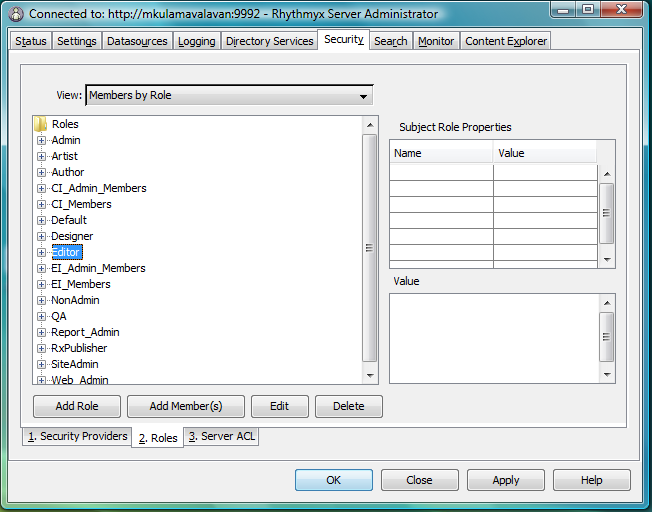
Step 5: Add an Active Directory user to a Role
- Select Security tab/ 2. Roles tab.
- Select the Editor role and click Add Member(s) button.
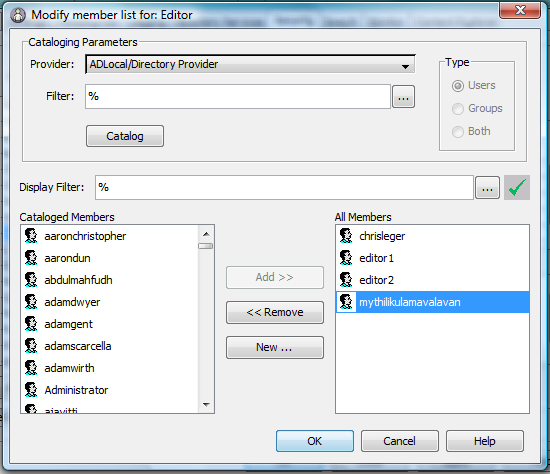
- From the Provider drop down, select Directory Provider created in Step 1, and then click on Catalog button to show the list of Active directory users.
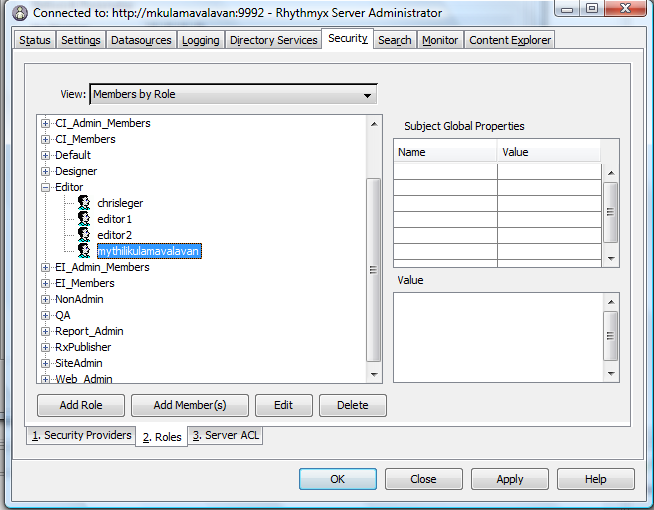
- From Cataloged Members List add an Active Directory user to Editor Role.
- For example in the screen-shot given below you will see mythilikulamavalavan an Active Directory user added to editor role.
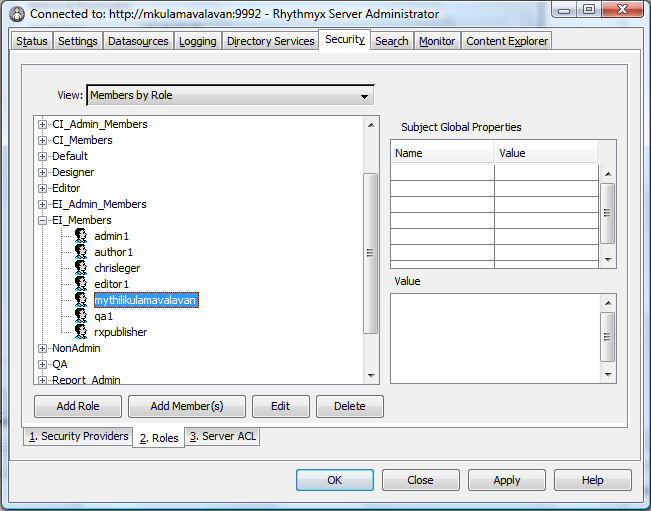
- You can associate an Active Directory user to any type of role associated with a community. To do so
- Select a specific role (EI_Members) and follow steps from 2 to 4 in this section.
- For example you will see in below screen-shot, an Active Directory user mythilikulamavalavan added as EI_Members role which is associated with Enterprise Investments Community.
Step 6: Test authentication by Logging in to Rhythmyx
- Log in to Rhythmyx using Active Directory credentials.
Note: For more information on integrating Rhythmyx with LDAP please refer from page 87 to 138 of Rhythmyx Administration Manual
